With the arrival of 5G and the Internet of Everything, mobile networks are no longer limited to traditional cellular access. In fact, many people may not realize that when they connect to the internet through Wi-Fi, they are already benefiting from the capabilities of the 5G core network.
Behind this seamless experience lies an often overlooked but critical component of 5G architecture: non-3GPP access. Acting as an “invisible bridge,” it enables diverse access technologies to converge into a unified 5G core.
What is Non-3GPP Access?
Under 3GPP standards, the 5G core network is designed not only for traditional cellular access technologies such as 4G LTE and 5G NR, but also for non-cellular connections. These are collectively referred to as non-3GPP access technologies and typically include Wi-Fi and fixed broadband networks.
In simple terms, non-3GPP access allows devices to connect to the 5G core without relying on cellular radio. Depending on the security and ownership of the access network, non-3GPP access is classified into two types: trusted and untrusted. Understanding the difference between them is essential for enterprises planning secure and flexible 5G network deployments.
Trusted vs. Untrusted Non-3GPP Access
Untrusted Non-3GPP Access
Public Wi-Fi networks—such as those in airports, hotels, or coffee shops—are typical examples of untrusted non-3GPP access. These networks are outside the direct control of mobile operators and therefore require additional security mechanisms.
Key characteristics include:
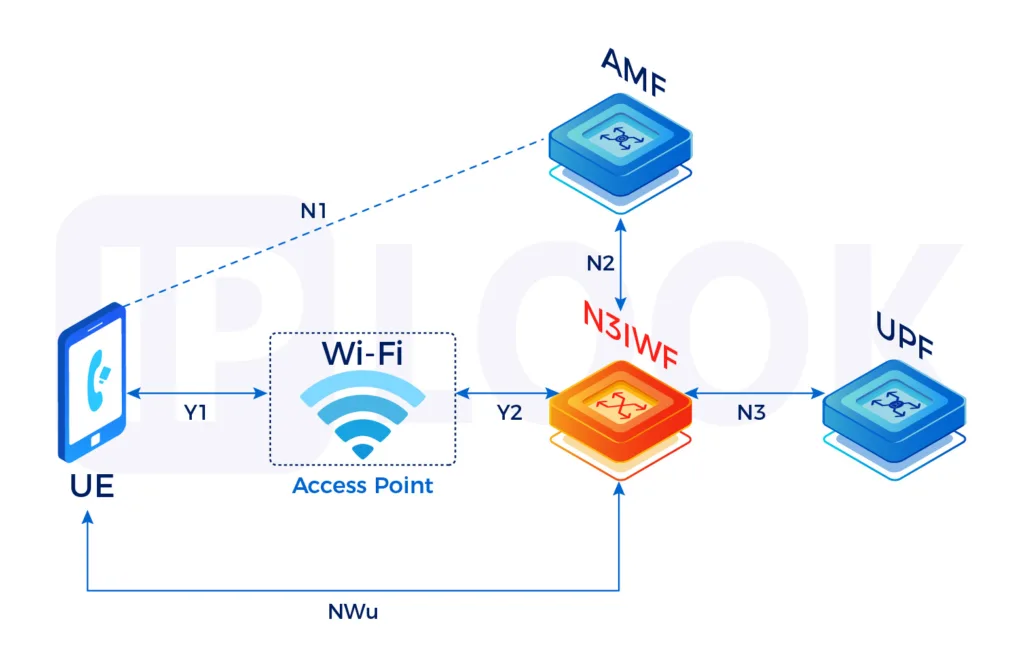
- Connectivity to the 5G core via the N3IWF, which acts as a secure gateway
- Establishment of IPSec tunnels between the UE and N3IWF to protect user data
- Use of EAP for secure control signaling
- Transmission of user traffic over GRE tunnels
This approach ensures security but introduces additional signaling and encryption overhead.
Trusted Non-3GPP Access
Trusted non-3GPP access is typically deployed in environments fully managed by operators or trusted partners, such as enterprise Wi-Fi networks. In these scenarios, security is enforced at the access layer, enabling more efficient integration with the 5G core.
A typical trusted access architecture includes:
- UEs that support NAS signaling
- Trusted Non-3GPP Access Points (TNAPs)
- A Trusted Non-3GPP Gateway Function (TNGF) on the core network side, which provides similar functionality to N3IWF but without encrypted IPSec tunnels, significantly reducing power consumption on terminals
- Standard WLAN security mechanisms (such as WPA3) between the UE and TNAP to ensure air-interface protection
This model allows enterprises to seamlessly integrate private Wi-Fi and 5G networks, delivering consistent user experience, simplified management, and higher efficiency. IPLOOK’s solution is designed for rapid deployment in such environments, helping enterprises accelerate the construction of converged access networks. In practice, standardized solutions supporting non-3GPP access, including those from IPLOOK, can be used to implement such architectures and support the gradual evolution toward converged 5G access networks.