Our High-Performing Core Network
Fully virtualizable on VMware, K8S, Docker and OpenStack containers
Voice over LTE(VoLTE)
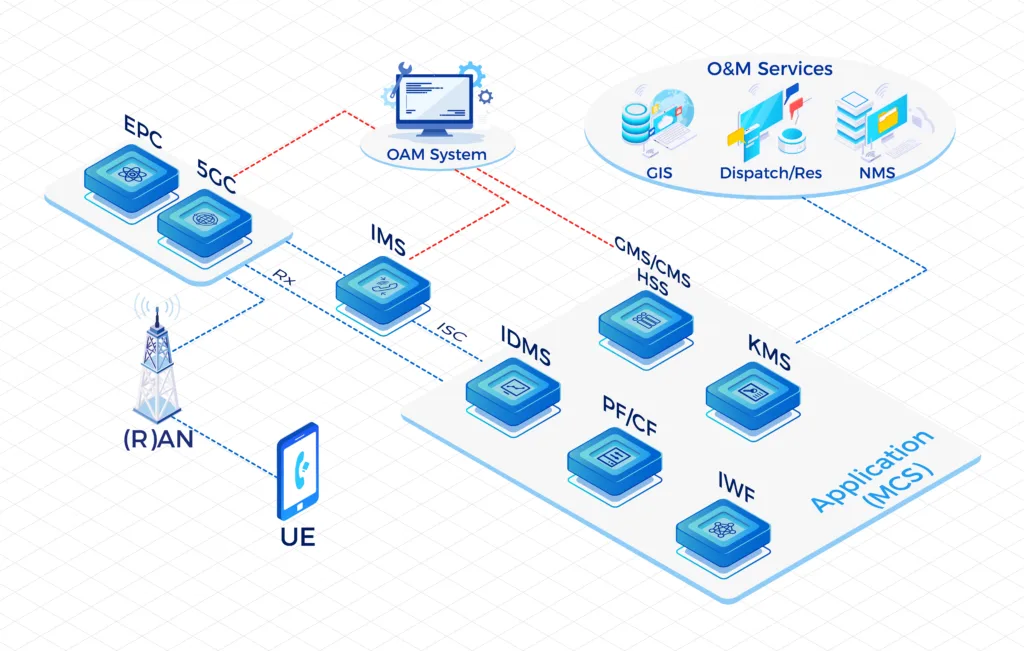
VoLTE (Voice over LTE) is a voice service based on IP Multimedia Subsystem(IMS). It is an IP data transmission technology that does not require 2G/3G network and all services are carried on 4G network, which can realize the unification of data and voice services under the same network.
Key Benefits

100% cloud implementation of IMS core deployment

Convergence of mobile and fixed access networks

Deliver seamless, uninterrupted roaming

Support hypervisor and dynamic lightweight Linux Containers

Simplify managing interconnect network topology

Carrier Grade Reliability Support for multimedia services
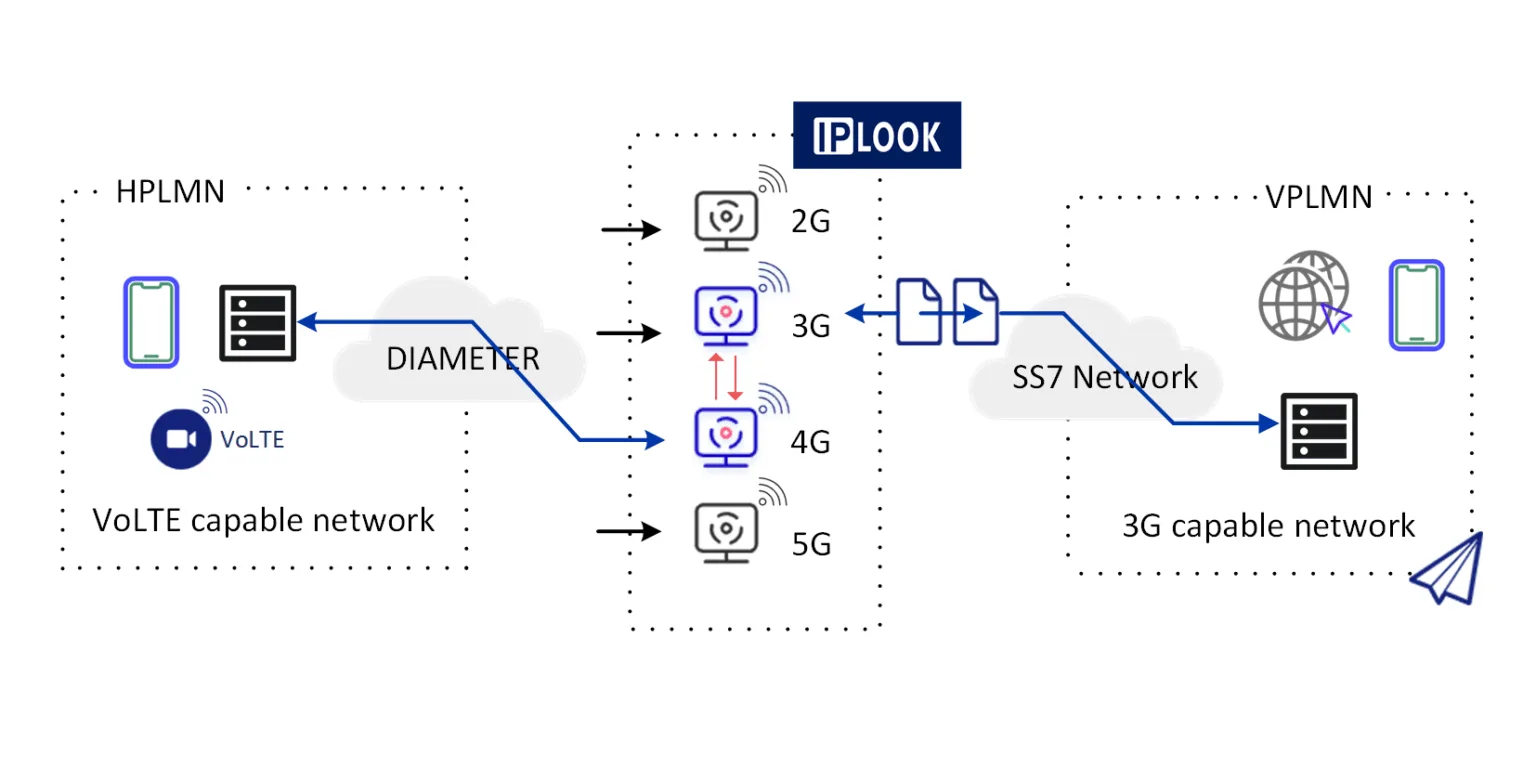
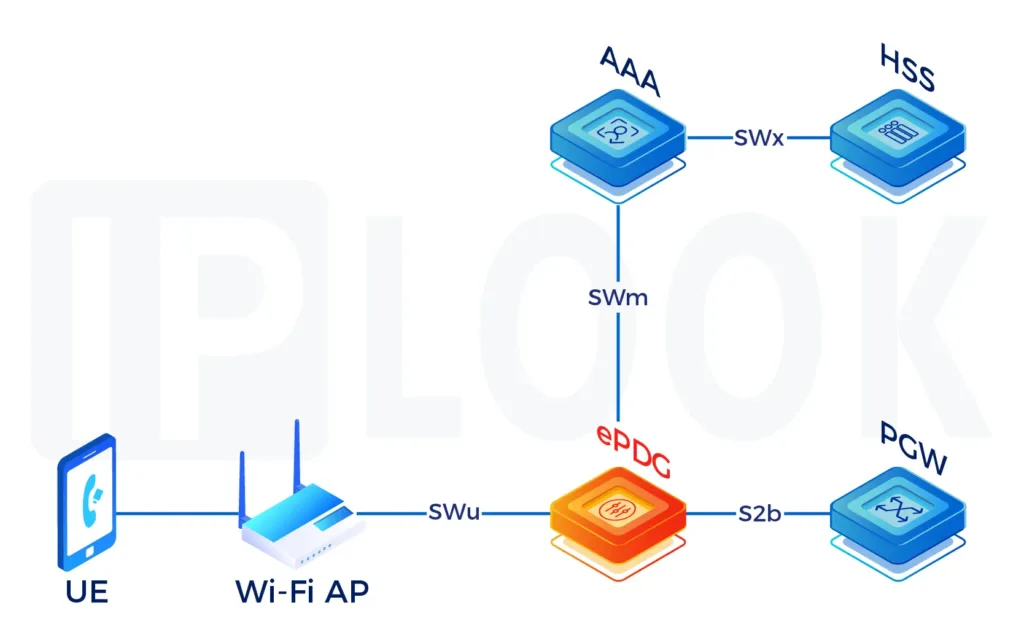
IPLOOK's vIMS solution Enable Voice over LTE(VoLTE) Roaming
- The flexible IPLOOK VoLTE Roaming solution supports a variety of inbound and outbound 4G voice roaming models that ensure a consistent and seamless user experience while roaming. It also helps grow ARPU and prevent the churn of high-value subscribers by expanding HD voice services beyond an operator’s own borders. TNS VoLTE Roaming and its supporting IMS core elements play a critical role in the evolution of voice from circuit switched to IP-based cellular networks in 4G and beyond.
Features
Comply to 3GPP R14 Standard
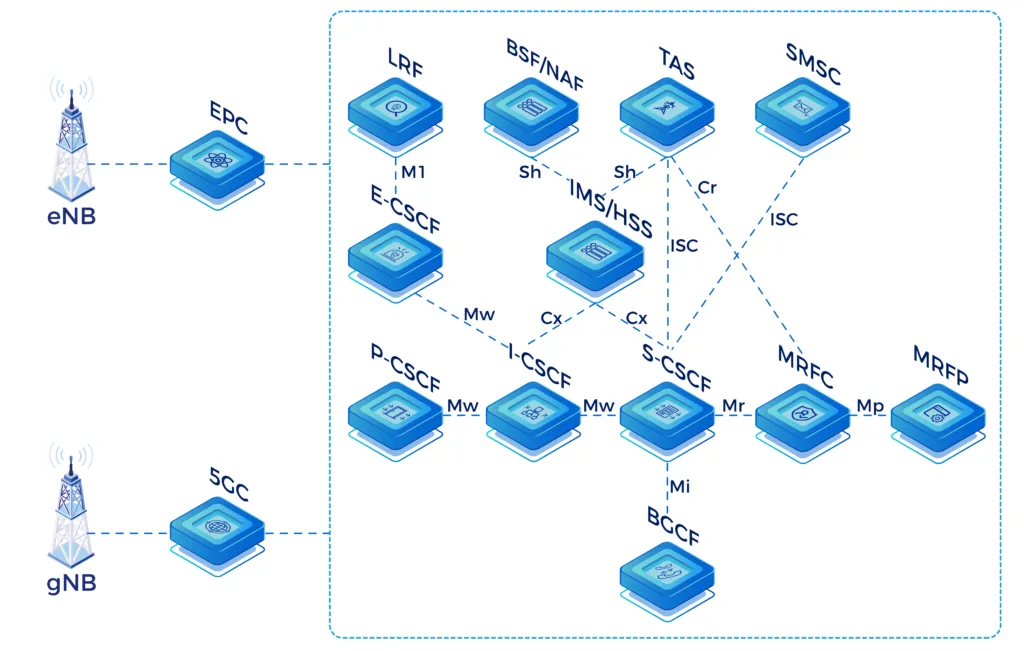
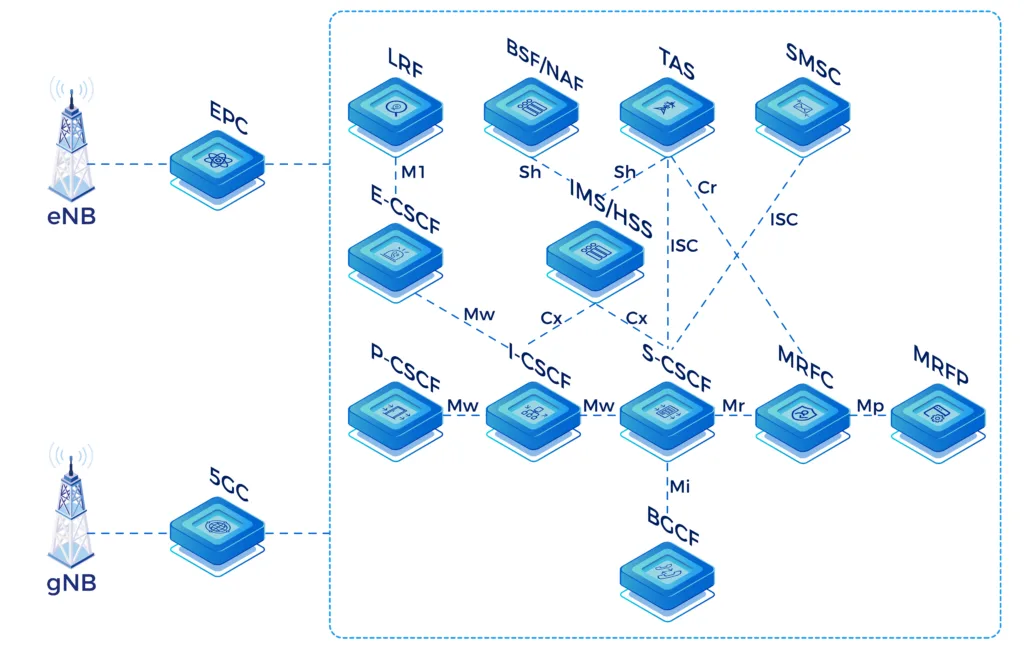
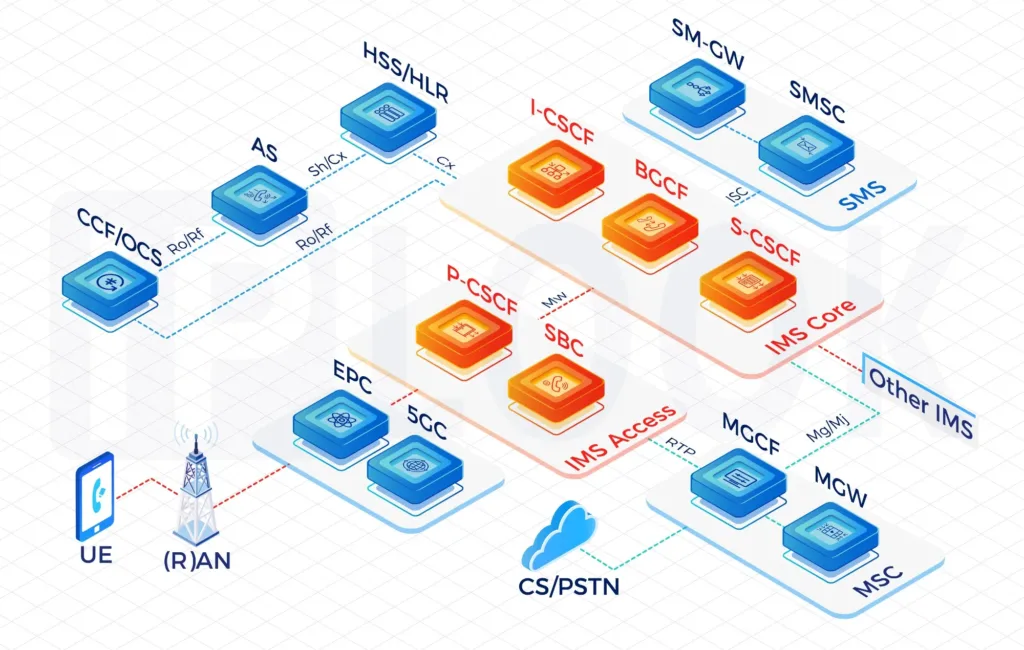
Application Servers
- IP-SM-GW: Provides SMS services for VoLTE and exciting devices and allows interworking towards other networks based on SMPP
- MMTel/TAS: Provides rich supplementary services, e.g., call forwarding and call barring and acts as a conference-factory for VoLTE handsets
- MRF: Provides network announcements and conferencing. Implemented according to RFC4240 (Basic Media Services in SIP) and set up as combined MRF-controller (MRFC) and -processor (MRFP)
- SR-VCC: Enables seamless early or mid-call handover from 4G/5G to 2G/3G and acts as a media-anchor for voice calls
- LI: Provides X1 to X3 interfaces towards the mediation function
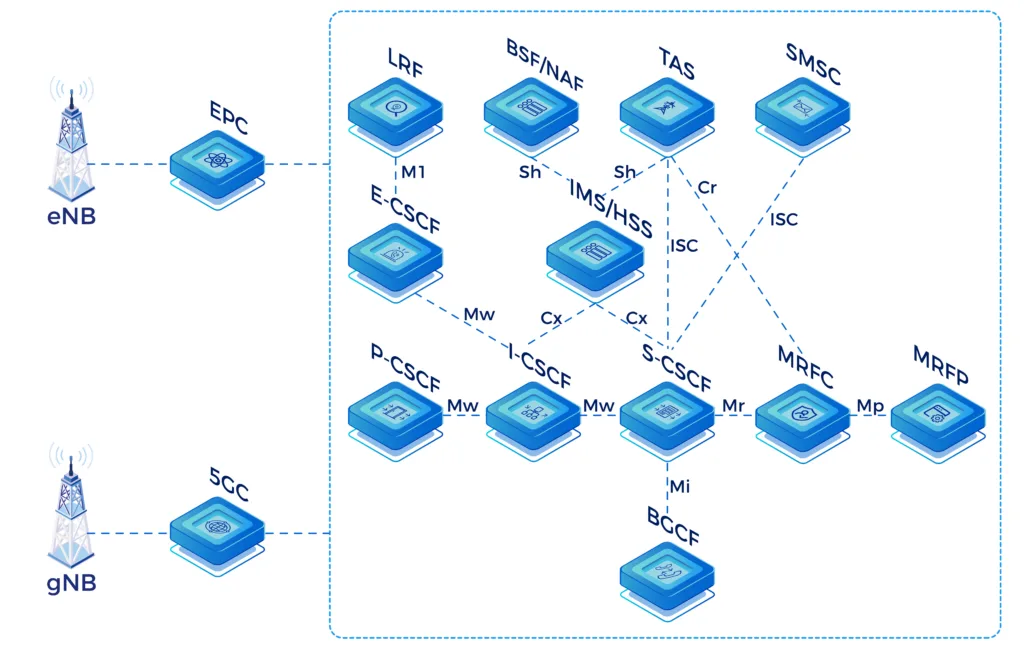
- I-CSCF: Provides full Cx/Dx interface support and selects S-CSCF based on user capabilities and load
Interfaces
- Rx: Between PCRF and P-CSCF
- ENUM: Between S-CSCF and ENUM-DNS server
- Sh: Between AS and HSS
- ISC: Between AS and CSCFs
- Gm: Between SBC/P-CSCF and UE (via EPC/PGW)
- Cx/Dx: Between CSCF and HSS
- Mg/Mj: Between CSCF and MGCF for PSTN-IMS interconnect
- SNMP: Towards Network Management System
- Ro: Between CSCFs and IN/OCS
- Rf: Between CSCFs and CCF
I/S/P-CSCF, BGCF, SBC, AS NE Functions
- I-CSCF: Provides full Cx/Dx interface support and selects S-CSCF based on user capabilities and load
- S-CSCF: Provides flexible application execution using a standards-based ISC interface and allows optional charging integration with standard Ro/Rf interfaces
- P-CSCF: Provides full transcoding support for AMR/AMR-WB based on a separated RTP worker
- BGCF: Adds interworking functions (flexible in- and outbound routing options) and provides topology hiding